With 67% of organizations seeing an increase in cyberattacks over the last twelve months, having a cybersecurity solutions provider on call is becoming more and more critical. Bad actors do not discriminate between large or small businesses either – any organization is fair game.
However, if you’re not an IT expert, finding a quality cybersecurity solutions provider can be challenging – not to mention, time consuming! To help you pilot the minefield of managed IT providers promising to secure your cyber assets, we have assembled this FAQ article. Below, you’ll find the most common questions you can ask an IT partner – and get an idea of what you can expect in response.
Are you ready to cut through the noise, ask the right questions, and make informed decisions to safeguard your business? If so, let’s get started.
1. What specific IT services does your company offer and how do they align with our business needs?
Before you can finalize your cybersecurity technology solutions, it’s vital that you understand exactly what they offer. One partner’s service offerings might not be exactly the same as another’s, or they could have a unique industry focus that could apply to your organization.
In response to this question, an IT company might list these types of cybersecurity services:
- Compliance guidance & best practices
- IT infrastructure security analysis
- Network security support (like firewalls)
- Spam filtering, such as with Barracuda
- Virus protection protocols
- And more!
Experienced providers will align your business needs by understanding your goals and challenges. With that in mind, they can offer a customized set of solutions that offers the best protection for your unique environment.
2. How will your team integrate with our existing IT staff and/or infrastructure?
For organizations with a smaller IT team, software maintenance and daily support can take away their high-value attention from necessary cybersecurity projects. Having an outsourced IT team dedicated to mundane or intensive security tasks can provide more bandwidth for your current IT.
As for your IT infrastructure, a provider should do what they can to integrate themselves with your environment. The goal would be to augment your current IT capabilities without drastically changing your IT before understanding your security goals.
3. How do you ensure that our business remains compliant with necessary regulations and laws regarding data and IT infrastructure?
A cybersecurity solutions provider should do everything in their power to ensure your business remains compliant. From title companies to banks to professional service firms, compliance with data regulations is paramount. With $1.4 billion in suspected wire fraud in 2022 alone, finding cybersecurity solutions is not something to put off!
How can a provider show that they are experts in compliance? They might have specific certifications or partnerships that represent their values.
For example, our team at Premier One is SSAE 16 (SOC) 2 Type II compliant. This means that we can work as your IT team right alongside you to ensure your compliance with those strict industry guidelines and best practices.
4. How does your incident response work in the event of a security breach? How quickly can we expect your team to respond?
An experienced cybersecurity solutions provider will explain their clearly outlined process that activates in the event of a security breach. This plan should be proactive and include:
Immediate threat containment
Breach investigation
Mitigation steps
And post-incident analysis to prevent future occurrences
Speed is of the essence in these situations, so a provider should promise a rapid response time and assure their availability to minimize potential damage and downtime.
To visualize our dedication, we offer real-time analysis on our response times on our homepage. If you’re curious, here is a recent snapshot on a regular business day:
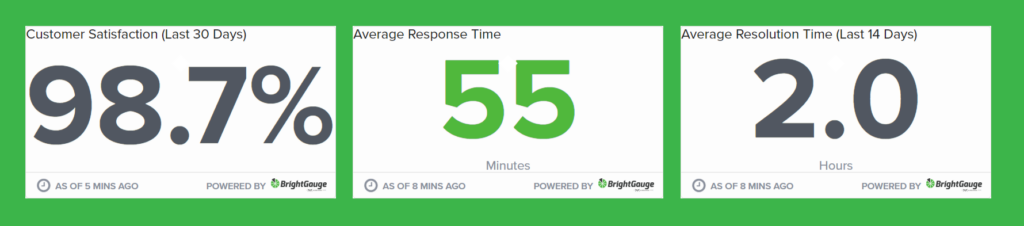
5. How will your IT services scale as our business grows? Can your solutions accommodate future expansion?
For a successful long-term partnership, a managed IT provider should explain their flexible solutions once your company grows. This can involve adding more users, managing more data, or integrating new technologies.
They should also ensure that any systems or protocols implemented at the beginning of your partnership won’t hinder your potential expansion, but rather, will evolve alongside it.
Whether your employees need a password manager, or want to take advantage of the secure cloud options within Azure or Microsoft 365, a managed IT provider can help.
Consider a Cybersecurity Solutions Provider with 30+ Years of Experience
Through these key questions, we’ve highlighted the importance of open, in-depth conversations with potential cybersecurity partners. Your business’s digital safety hinges on making informed choices, and asking these questions will empower you to do so.
Whether you’re a small business manager or an IT leader, being proactive in your approach to cybersecurity is the best way to navigate service offerings.
For example, a provider must offer tailoring to your unique needs, integrate with your existing IT infrastructure, and ensure regulatory compliance. Swift incident response in the face of security breaches, along with scalable solutions that grow with your business, are additional non-negotiables.
Need more assistance finding an experienced cybersecurity solutions partner? Our IT experts have been supporting businesses in Topeka, Kansas, and the rest of the country since 1991. Learn why businesses choose Premier One today!







